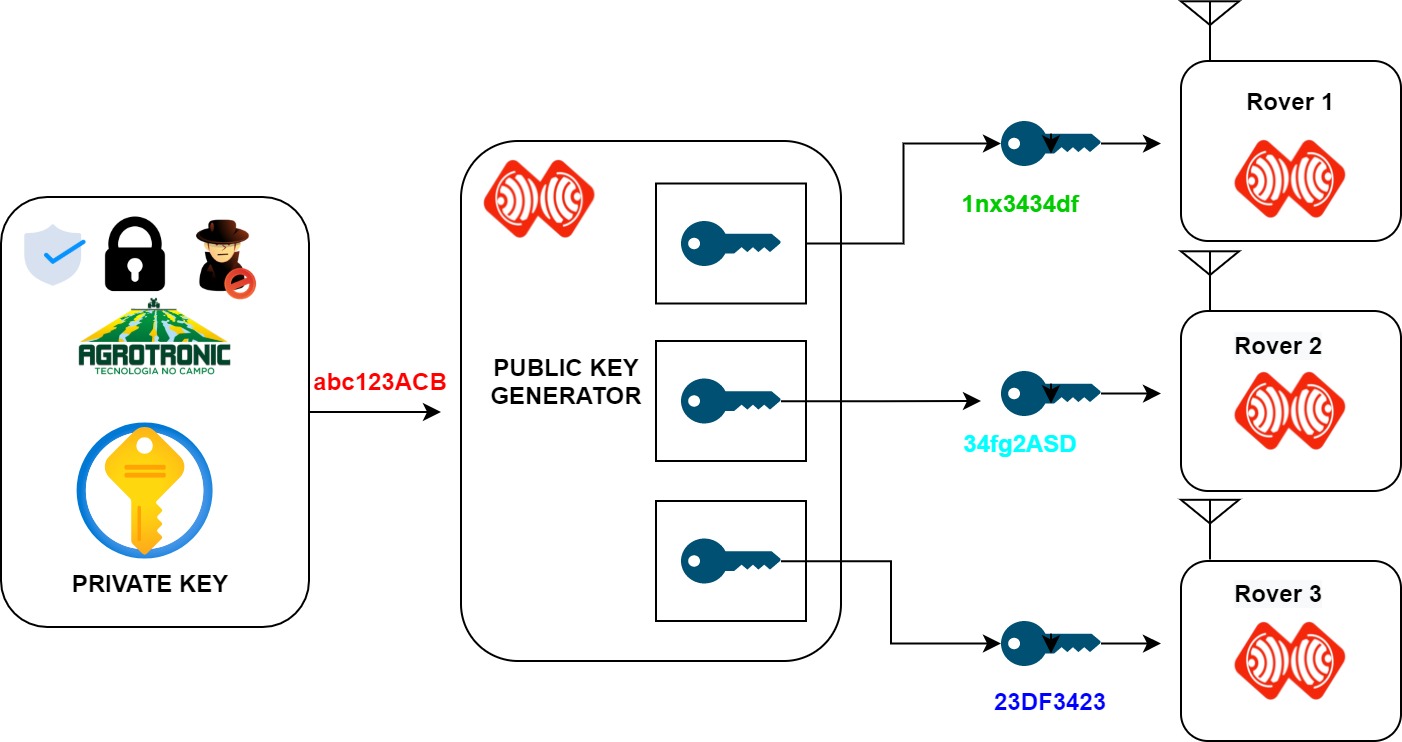
Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen
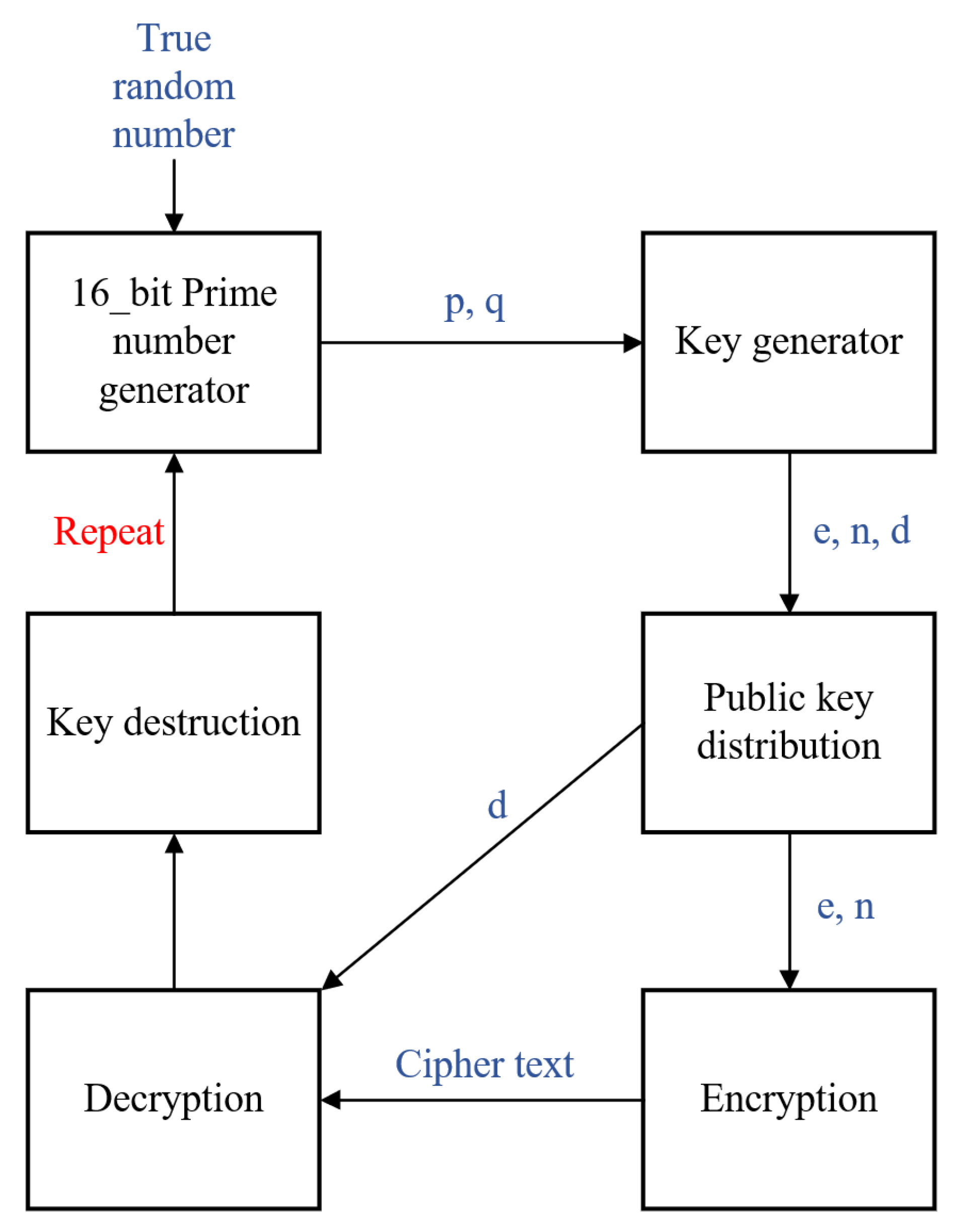
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices